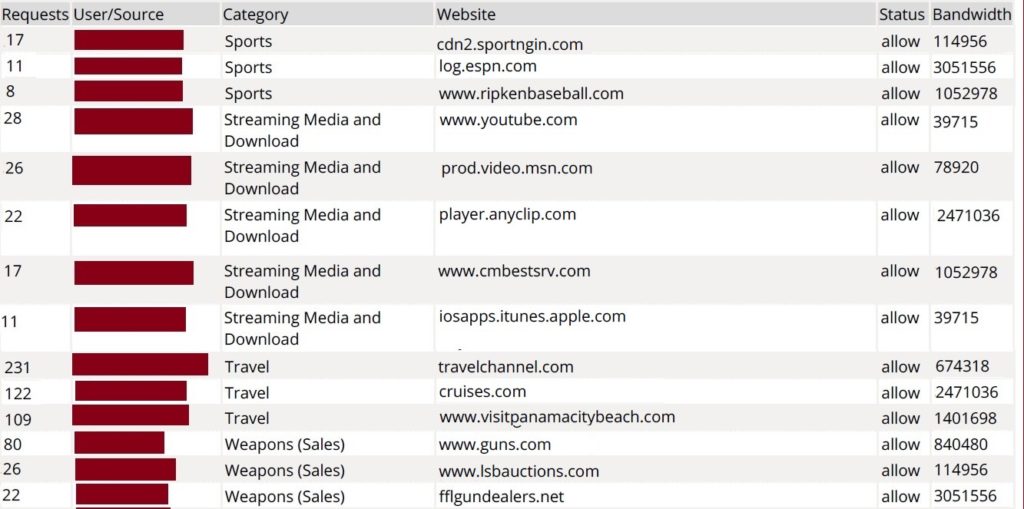
I recently spent time building FortiAnalyzer reports to let management see which devices are spending the most time browsing non-work websites. I was really surprised how hard it was to find information on this topic. No default reports on the FortiAnalyzer gave the level of detail I wanted without running the User Detailed Browsing Log …Read More…
Category: Computers
The #1 Computer Security Threat Just Evolved – RCE Worm
Let me tell you a story about a worm. This worm’s name was Welchia, and it came into the world late one night in mid-2003. I was early career IT at that time, working Tier 2 Helpdesk in a very large (hundreds of thousands of users) enterprise. We had server farms across the …Read More…
How to fix vSphere and vCenter datastore reverting to old size
Symptoms: You increased the size of a datastore in the past, but now when you open vCenter, you see the old (smaller) size displayed. There may be low disk space warnings. Web client for vCenter 6.5 and vSphere 6.5 and probably vCenter 6.0 and vSphere 6.0 If you refresh the datastore information, the correct size …Read More…
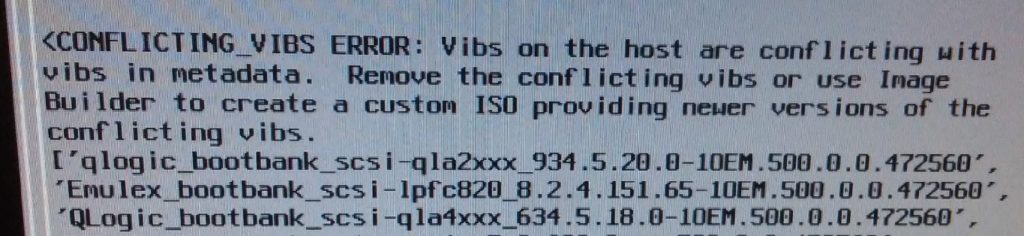
HP DL360p g8 ESXi 5.5 to 6.5 upgrade conflicting_vibs_error
Had to troubleshoot a few HP DL360 servers recently during a vSphere upgrade. They refused to upgrade to vSphere ESXi 6.5 with a conflicting_vibs_error Symptoms: After selecting “Upgrade ESXi and preserve the existing datastore”, the system scan presented the following error: <CONFLICTING_VIBS ERROR: Vibs on the host are conflicting with vibs in metadata. Remove …Read More…
Is your IT person holding the network hostage?
Problems with your PC Support and IT staff “Step 1: Change all the passwords…” This is an inside joke for IT professionals. It refers to job security. If you are the only person who has the keys, your management will think twice before they fire you. With that level of job security, you can close …Read More…
4 mistakes people make when hiring a computer services company
Mistake #1: After choosing an IT support provider, you no longer need to be involved in the management of them. As with any department you manage, your IT support provider will need oversight as well as clear and consistent communication. When you stop being involved with your IT support provider, expectations are not clearly …Read More…
What you should know about Cloud Computing and Office 365
Traditionally, if you needed a new server for your business, you bought an expensive piece of equipment, screwed it into a rack, turned it on, and installed the software. Now we have cloud computing, which makes the server software independent from the equipment. You could have ten servers worth of software running on one piece …Read More…
Can You Make Our Nation Safe from Hackers?
This article is meant for you as a voting citizen, rather than you as a home user or business owner. Nationally, for our own security, we need to make changes to the way our IT infrastructure is managed. Proposal Nationally, identify potential computer impacts in a tier structure. Each utility, large company, and government …Read More…
The Ultimate Way to Protect Against Computer Theft
Over the last five years, hard drive encryption has become mainstream for enterprise-size businesses. I recommend encryption for any business or personal computer which holds critical information, but it is important to understand that it only protects computers that have been physically accessed – it doesn’t help against viruses or attacks against the software. How it …Read More…
Small / medium business security concerns
I recommend reading over this CNBC article about the latest trends in small business malware attacks. This is becoming more of a threat over time, and should concern all business owners. cnbc.com: A wave of new viruses is targeting small businesses The article unfortunately doesn’t discuss defense tactics that the average small business can …Read More…