The Ultimate Way to Protect Against Computer Theft
Over the last five years, hard drive encryption has become mainstream for enterprise-size businesses.
I recommend encryption for any business or personal computer which holds critical information, but it is important to understand that it only protects computers that have been physically accessed – it doesn’t help against viruses or attacks against the software.
How it works

The hard drive is where your critical information is held. This information is stored in a logical, well defined matter, in data files that are stored just like the files you see when you open your C:\ drive. A very simple hack is to simply unscrew the target hard drive, plug it into the bad guy’s computer as a secondary drive, and access the files from D:\. This takes skills learned in the first year of a PC tech’s career. It bypasses your log-on passwords and any network security completely. This is what hard drive encryption protects against.
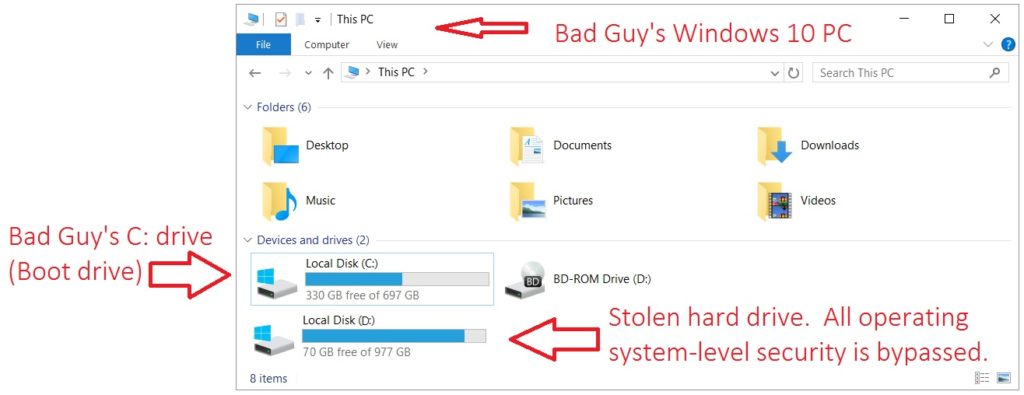
An encrypted hard drive is split into two sections – a very small decryptor section at the beginning, and the main storage section. The main storage section has the encrypted data, but not any tools to decrypt it. The decryptor section has the knowledge to decrypt, but it doesn’t know the key.
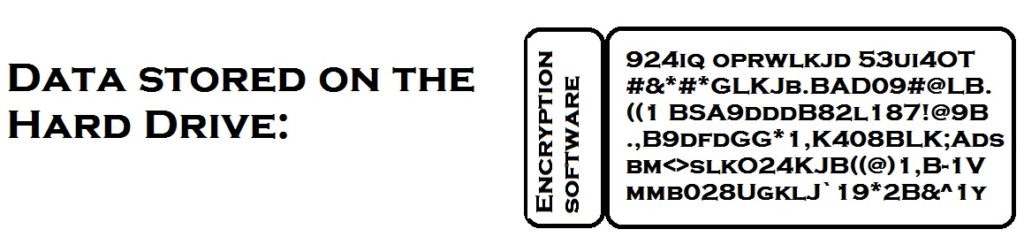
The key is provided by an outside source such as you or a server on your network.
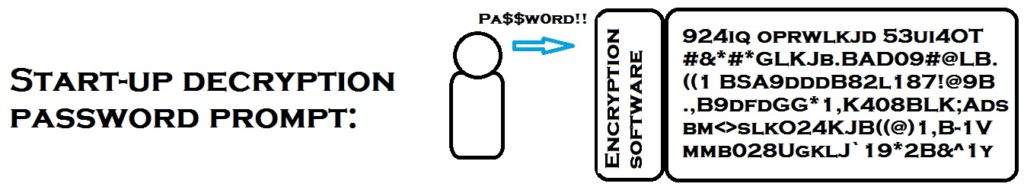
Once the key is entered (when the computer boots up), the encryption software will keep using it (storing it temporarily in RAM memory) until the computer is powered off.

Automatic decryption once logged on is the reason why hard drive encryption is only a partial solution for security. Once the computer is turned on, the key is entered, and the operating system (such as Windows 10) is running, all files on the hard drive can be accessed across the network or by the logged on user. So all the normal security measures such as patches, antivirus, firewalls, and security policy are still necessary.
Bottom line: If there is any risk that your computer or hard drives could be physically stolen, invest in hard drive encryption.
There are several options ranging from workstation protection (Bitlocker, available with Pro versions of Windows 10), to extremely secure virtualization-compatible products like HyTrust DataControl for $400-$1000 per server. Work with a professional to make sure you have a good backup first, and a plan to troubleshoot issues. Losing the key or corrupting the encryption software can cause a loss of all data.

