In many organizations, the servers and especially the storage area network (SAN) are critical. The thought of installing firmware on these systems or performing a major operating system upgrade is incredibly scary to the IT staff. I was working at a company recently which was having trouble with their backup system. Their backup system did …Read More…
Tag: Frederick
Disaster Recovery Plan and Business Continuity in DC, Frederick, Baltimore, Rockville, and Columbia MD
“ “Two out of every five companies struck with a major disaster are unable to recover. Of the survivors, one third go out of business within the next two years. ” — Gartner Study – 1996 Availability and Integrity – why you need Business Continuity Plans and Disaster Recovery Plans. Did you know that Information Security …Read More…
VMWare and Netapp consultant in DC, Baltimore, Columbia, Frederick, and Rockville MD
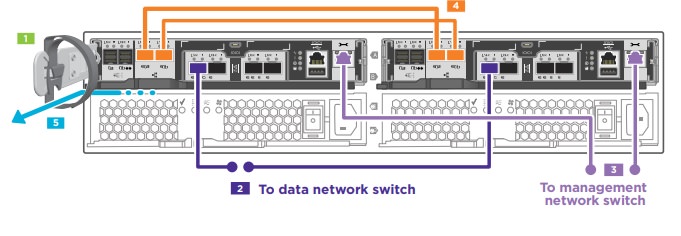
We install and configure Netapp Disk Shelves and VMWare vCenter and ESXi for small and medium businesses in Maryland and DC. (more about VMWare and virtualization later in this article!) Netapp installation, integration, and maintenance Kieri Solutions endorses Netapp products because they are designed to be highly available and have several options for nearly instantaneous …Read More…
SBDC – Intro to GDPR training – Frederick MD
If your business deals with the personal information of EU citizens, or you are not sure if GDPR applies, you should come! On May 25, 2018, new legislation aimed at giving individuals more control and protection over their personal data – the General Data Protection Regulation (GDPR) – went into effect. Is your …Read More…
GDPR and Human Resources
With GDPR moving into enforcement this month, many businesses in the United States are scrambling to perform damage control. Human Resources has unique concerns about GDPR – Do I need consent to collect personal information about our employees? – Are there extra steps required before providing employee information to outside benefits companies? – Are things …Read More…
Upgrade your IT Services for the New Year
Upgrade your computer management for the New Year! Businesses in our service area (between Rockville, Frederick, and Baltimore) can reference this advertisement for a free service visit (approx 1.5 hours) to fix small problems and talk about long term goals. Small and medium businesses struggle with their IT departments. They either can’t afford the salary …Read More…
Dell PowerEdge R730 PERC RAID online reconfiguration
This is a story about how we migrated a production server from RAID-1 to RAID-5 without losing data, using the PERC H730 controller. Recently, we pushed a Dell server’s PERC RAID controller to its limit. (After making a verified good backup, of course). Originally, the server’s hard drives were set up as a RAID 1 …Read More…
4 mistakes people make when hiring a computer services company
Mistake #1: After choosing an IT support provider, you no longer need to be involved in the management of them. As with any department you manage, your IT support provider will need oversight as well as clear and consistent communication. When you stop being involved with your IT support provider, expectations are not clearly …Read More…
What you should know about Cloud Computing and Office 365
Traditionally, if you needed a new server for your business, you bought an expensive piece of equipment, screwed it into a rack, turned it on, and installed the software. Now we have cloud computing, which makes the server software independent from the equipment. You could have ten servers worth of software running on one piece …Read More…
The Ultimate Way to Protect Against Computer Theft
Over the last five years, hard drive encryption has become mainstream for enterprise-size businesses. I recommend encryption for any business or personal computer which holds critical information, but it is important to understand that it only protects computers that have been physically accessed – it doesn’t help against viruses or attacks against the software. How it …Read More…