Coming in 2020, the DoD Cyber Security Lead has announced the Cybersecurity Maturity Model Certification (CMMC) for Dod Contractors. Learn more…
Tag: cybersecurity
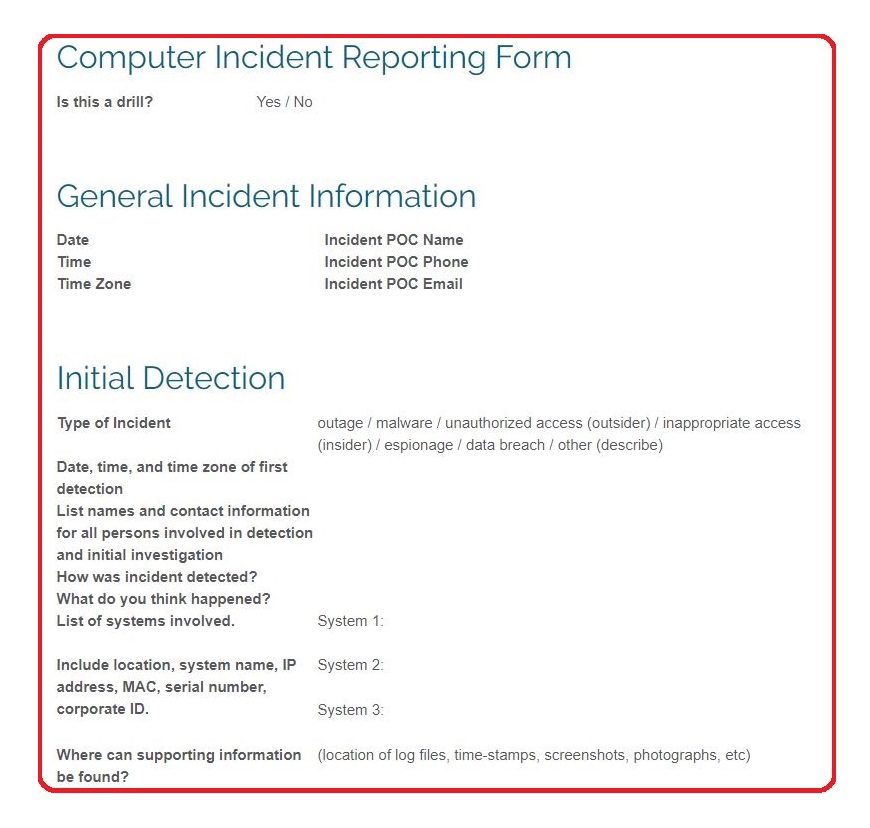
Best Free Computer Incident Response Templates and Scenarios
Welcome! You are looking for a free Cybersecurity Incident Response Template and getting frustrated because all the other websites want you to register on an email spam list. Or their templates are in PDF format and you’d have to re-write them from scratch. Annoying! I think you will be happy with my template – no …Read More…
Network hardening near Baltimore MD, Frederick, Rockville, Gaithersburg and DC
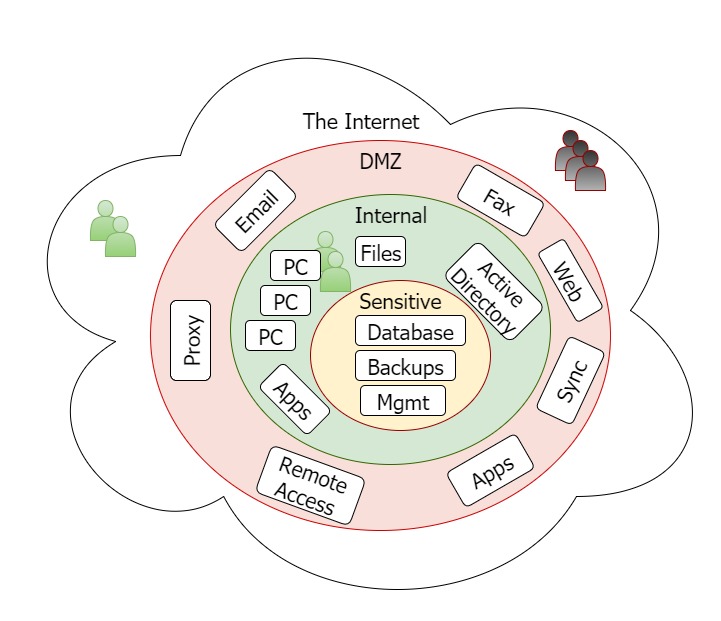
How to stop lateral movement through your networks Kieri Solutions implements deny-by-default firewalls and network segmentation for government, small, and medium businesses. This is a specialized skill which requires very strong knowledge of a broad range of platforms as well as network security. If you would like to chat about your network hardening and compliance …Read More…
Approaches to security policy
Here are common strategies for security policy, for better or worse. Plug the Holes This approach is used by enterprises and big business – those with a $10,000,000+ budget for their IT department. Enterprises need a full-functioned network. They need ten different versions of Microsoft servers and desktops, Office, Adobe, Internet Explorer, File sharing, Websites, and …Read More…