Network hardening near Baltimore MD, Frederick, Rockville, Gaithersburg and DC
How to stop lateral movement through your networks
Kieri Solutions implements deny-by-default firewalls and network segmentation for government, small, and medium businesses. This is a specialized skill which requires very strong knowledge of a broad range of platforms as well as network security. If you would like to chat about your network hardening and compliance project, email us at info@kieri.com
If you want to prevent damage from hackers and ransomware attacks, you need to perform network hardening and segmentation.
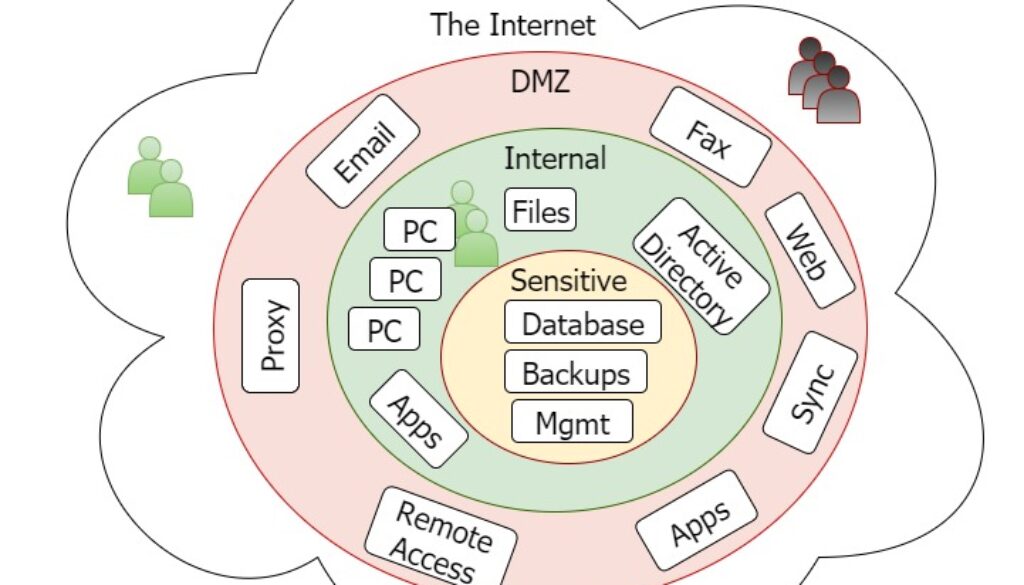
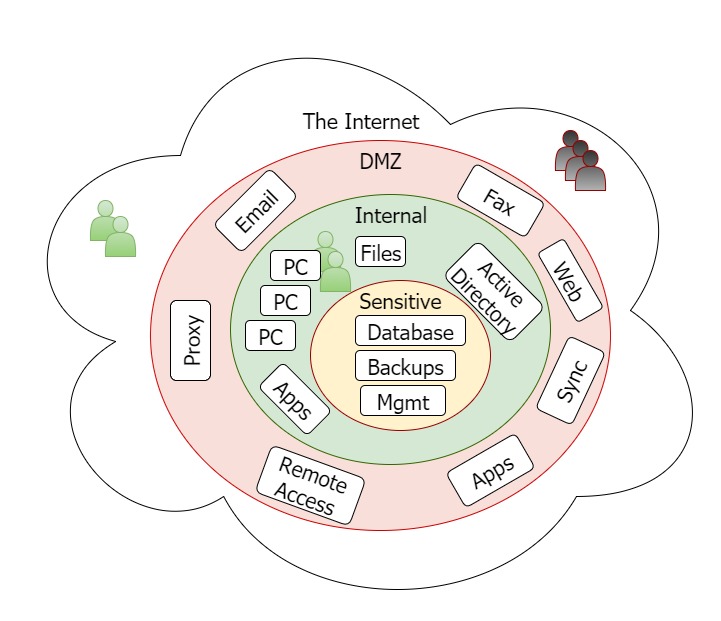
NIST security publications encourage ‘defense in depth’ as a best practice. They recommend creating multiple network segments with strong firewalls in between. The diagram above shows a cost effective segmentation design that is appropriate for medium businesses.
NIST control 3.13.6 Compliance
NIST and DFARs compliance projects require implementation of control # 3.13.6: Deny network communications traffic by default and allow network communications traffic by exception (i.e., deny all, permit by exception).
This is one of the most difficult cybersecurity controls to comply with. Almost all businesses have wide open (allow all) network communications, except for the external firewall. Open communication places the business at risk of data breach, intellectual property theft, insider threat, and extensive damage from malware attacks. Attempts to secure your network by denying traffic by default will often cause system outages unless you have expert assistance.
By separating your network into multiple segments, you limit the damage that could occur from cyber-security threats.
For example, many ransomware attacks will spread to every vulnerable computer in the same network segment as the original compromised computer. Rather than have your workstations AND server data destroyed, wouldn’t it be better to limit the damage to just a few workstations?
Several IT Cybersecurity compliance frameworks require the use of De-Militarized Zones (DMZ) and Secure Sensitive Networks. For example, if your business processes credit cards, the PCI compliance program will require that you separate credit card databases from externally-facing servers.
Deny-by-default DMZ Firewall
A secure DMZ is the first improvement you should consider. It is also an important step for PCI compliance. Your externally-facing servers are at high risk from Internet-based attacks. Once an internal server is penetrated and taken over by a hacker, they “pivot” to attack the rest of your network. Any penetration tester will tell you that once they are inside the network, the hard work is done.
Examples of servers that should be in a DMZ:
- Outlook Web Access and Outlook direct (Exchange Client Access Server)
- Remote access (Citrix terminal servers and Remote Desktop for users or IT staff)
- Application servers that transfer data to-or-from other companies
- Proxy servers
- Spam filters (Barracudas etc)
- Electronic faxing
- Any web server that can be reached from outside
- Servers that synchronize with “the cloud” or other businesses
How does a DMZ deny-by-default policy work?
The outside firewall (between your company and the Internet) should already be using deny-by-default policies, at least for traffic coming in from the Internet. We will review this to see if it is possible to tighten up any of the policies. For example, many companies allow remote access to a terminal server from anywhere on the Internet. This is extremely risky. We would recommend reducing this remote access to specific network addresses (such as vendor networks) and using VPNs for traveling employees.
Where it makes sense, we also want to restrict outbound communication through your firewall. Once a hacker has accessed your sensitive information, they generally want to make a personal copy of it. They do this by sending it through your firewall. Blocking unusual traffic makes it harder for the bad guys to perform a data breach.
Creating a DMZ adds a second firewall layer between your externally-facing servers and your internal network. This restricts the network traffic that moves between DMZ servers and the rest of your network.
How is a DMZ with strong firewall implemented?
Very carefully. This is not a fast process. The last time we created a DMZ for a medium sized business (500m/year revenue and 10 servers inside the DMZ), it took three weeks, about 100 billable hours, and a two-month on call period to complete. But we researched and tested everything thoroughly as we went, which minimized user impact. If anyone tells you that this is a fast or easy process, they are probably leaving allow-all rules between the segments, which defeats the entire purpose.
- Research and planning phase: Carefully review each server, and each server that they communicate with, to identify normal communication channels and port usage. Create written back-out plans so that if business is impacted, we can flip a switch and get the servers communicating until we find a solution.
- Establish DMZ network: Migrate server networking to the DMZ. Other servers will need to update their connection information for the migrated server. Test thoroughly.
- Enforce deny-by-default policies: Create a firewall policy set for each DMZ server which allows only necessary communication between the outside and the inside. Test thoroughly (this includes restarting services and servers to trigger startup communications).
- Monitoring and responsiveness: Engineer is on-call for at least a month to assist with infrequent situations such as month-end accounting jobs.
- Documentation and training: Provide configuration management information, firewall and switch configs, and train your staff to manage the new systems.
Sensitive systems internal layer
The next segmentation improvement is to set up a sensitive systems internal layer. This network layer is for the most critical systems: high value targets such as your customer database, proprietary designs, and backups. Core IT systems such as VMware, switch, and firewall management can also be protected here.
How is internal segmentation implemented?
The process is essentially the same as the DMZ, but for the most sensitive systems rather than the least sensitive systems. Servers are only good candidates for this if they have limited communications. For example, an ideal database server would only have one communication channel open – between it and an application server.
A server that is accessed on multiple ports by regular users (such as a file server or directory server) cannot be fully secured, so it should stay on the internal network.
Internet of Things – a developing risk
The problem with IoT is that most of the devices are programmed to “call home” to their vendor. Depending on the device, they might download updates automatically, or even be remotely managed by the vendor. If the vendor is compromised, each of their devices could be a source of infection to your network.
For example, even if you have a firewall that protects you against inbound threats, your security camera probably opens an outbound connection to its vendor company each day. Normally this is a good thing – it lets the vendor install patches or centrally manage the device. But if something goes wrong at the vendor, the device could serve as an access point into the inside of your network.
In the last two years, the Internet of Things (IoT) has exploded. Your business might have some of these…
- Smart TVs
- VOIP phones
- Security cameras
- Personal assistant devices (Alexas, Siri)
- Printers
- Environmental systems
- Scanners
- Some “smart” firewalls such as FortiNet
- Smart backup devices such as Datto
- Network Attached Storage (NAS) such as Synology
- Tablets
- Battery back-up systems
- “Smart” lights
There aren’t established industry best practices for IoT devices yet, but we here at Kieri Solutions feel that they should be strongly separated from the rest of the network. Setting up an separate network just for IoT devices is an easy way to do this for your business.
Do I need to buy multiple firewalls or switches?
Most of the time, if you are working with business-quality firewalls and switches, we do not need to buy any new hardware. Most professional firewalls / routers such as Cisco, Sonicwall, FortiNet, and WatchGuard have built-in capability for multiple network segments. Most professional switches have VLAN capability, which we can configure for DMZ and sensitive network segments.
What is the next step?
Please consider Kieri Solutions for your network hardening and segmentation project. Our employees are trusted by the US military, universities, large, medium, and small corporations. We love after-hours work, change management, configuration management, and testing because they reduce risk and keep users working.
Email us: info@kieri.com
Call us: (301) 253-5150

Kieri Solutions is a cybersecurity and IT consulting company serving businesses in Maryland and Northern DC. Silver Spring, Rockville, Gaithersburg, Frederick, Baltimore, Columbia and other nearby cities in MD.
We also assist companies throughout the USA for remote-work projects such as virtualization, Azure, and security policy writing.