Multi Factor (MFA) App Password Missing or Blank – Office 365
Symptoms for missing Multi Factor Authentication (MFA) app password in O365:
- You enabled Multi-factor Authentication (MFA) on Office 365 (O365) portal or Microsoft 365
- MFA works, and your user(s) are able to log on to the office.com website using it.
- You don’t see the “app password” listed anywhere, and the Account Settings view seems to be missing that section.
- You set up a conditional access policy for Multi Factor, per the Microsoft how-to article.
What are app passwords in office 365 or Azure?
App passwords are unique passwords used to authenticate legacy software to Office 365.
The primary use case is Outlook 2010 , or Outlook 2016. For example, these could have been standalone deployments before Office 365 was adopted. These older versions of Office may not know how to handle a multi-factor prompt.
If your organization uses Office 365, I recommend installing the latest version of Office 365 from office.com. The latest versions know how to handle multi-factor and don’t need app passwords.
Most users don’t use app passwords.
What does missing app password look like?
You should be able to view or create app passwords from the user’s account settings in Office 365.
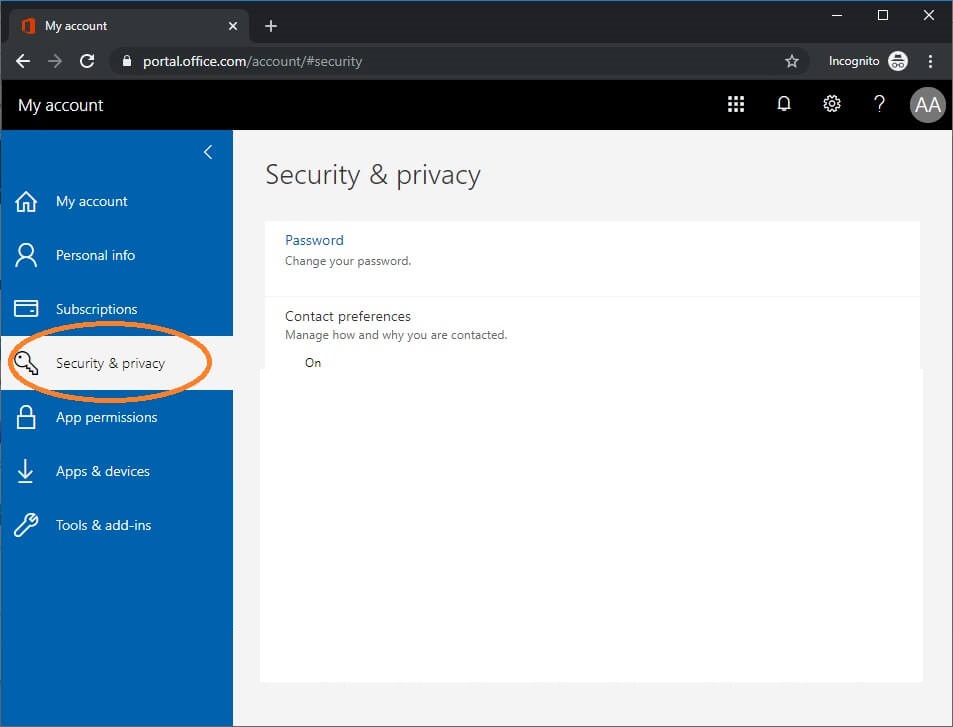
If you are having this issue, the area for app passwords is blank. The picture above shows a missing app password area. It should be right under Contact Preferences.
Root cause for missing multi-factor app password:
The Office 365 admin portal has two separate ways to enable MFA for users. One way is to use the Admin > Users > Multi-factor Authentication menu for individual users. The second way is to set up a Conditional Access Policy. Microsoft articles say to use the Conditional Access Policy, but there is a problem with that.
There appears to be a bug where app passwords aren’t enabled properly when you use Conditional Access Policies.
To fix the problem, you need to enable multi factor using the Users menu, not conditional access policies.
The good news is that you don’t need to abandon your conditional access policy entirely. Just use this fix for individuals who need an app password, not everyone.
How to fix missing multi-factor authentication app password in Office 365
To enable application passwords in O365, you need to use the Multi-factor authentication page in admin center.
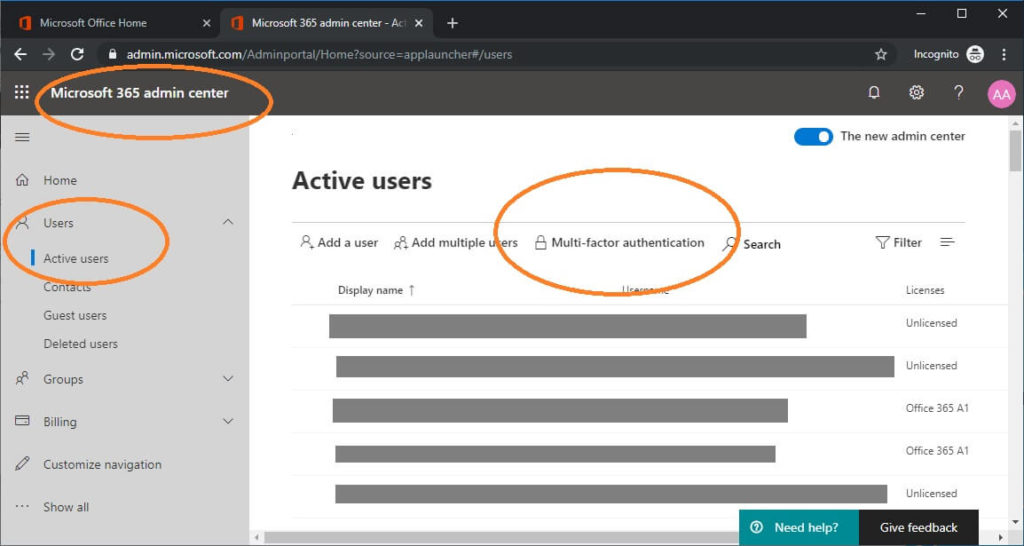
Navigate to Office 365, log on with your admin account
Click Admin from the menu
Click Users > Active Users from the menu
In the center, you will see a link to “Multi-factor authentication”. Click this link.
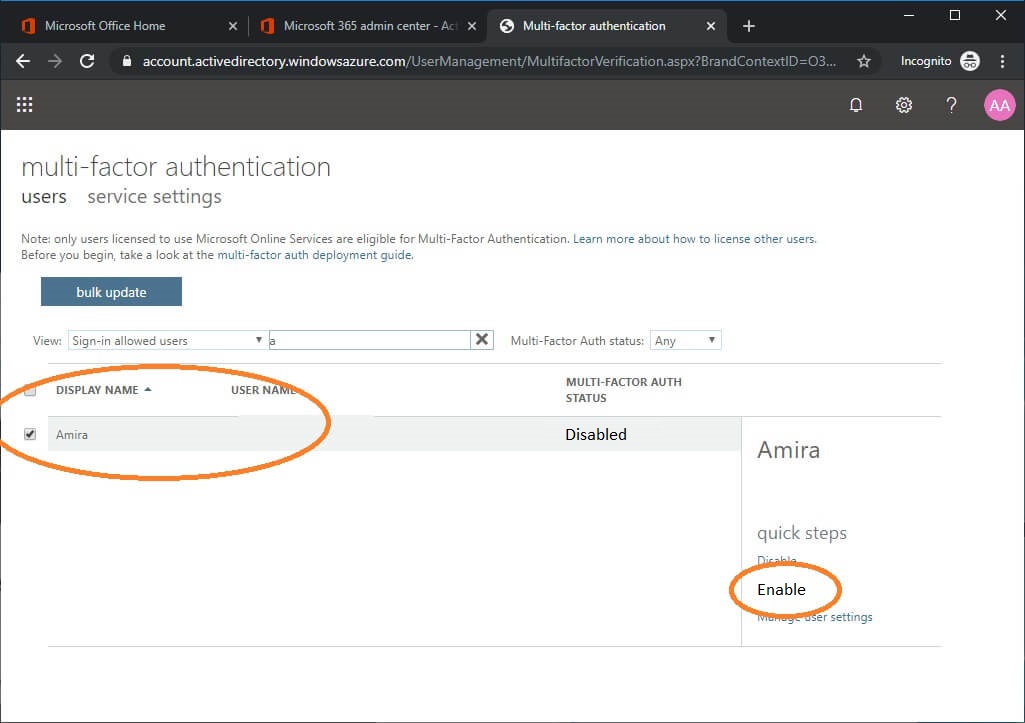
Your users list will display. You can filter for individual users here.
Pick the user that needs an app password and click “Enable”.
Enable the user here even if you have already set up a conditional access policy for MFA that includes the user.
For most organizations, you should be fixed now. When I tested, this took effect immediately and I create my app password as the user within 30 seconds.
Recently (May 2020 and later), we are seeing more complex issues that are not resolved by enabling MFA in the users area. Read on for information about fixing those issues.
Modern Authentication fix for missing O365 app password
Thanks to Rob Ryan for sending me these fix steps. Cheers!
Symptoms:
- The App Password is missing no matter if we enable or disable MFA from Admin Center > Users.
- Disabling MFA did not remove the requirement for multi-factor when we log on with an incognito browser.
- We could not find any conditional access policies, and no one had set up any.
- Tested email connectivity using testconnectivity.microsoft.com (Outlook test). This failed with an error saying that a conditional access policy denied access.
His account definitely had conditional access policies applied but they were hidden, possibly because his O365 license didn’t have Active Directory Premium 2 rights.
We eventually put in a ticket to Microsoft support, and they pointed us in the correct direction.
The issue was a setting under Office 365 Admin Panel. There is a setting for “Modern Authentication”, that needs to be turned off for some apps that have a different or older Exchange Authentication process.
(Admin center > Settings > Org Settings > Services Tab > Modern Authentication)
This setting can be found in the Admin Panel by clicking “Settings” in the left hand menu panel and then clicking “Org Settings” under the drop down menu. Then click on “Modern Authentication” in the list of settings. Toggle to “off” wait 2 – 3 hours.
Then to set “App “Password, go under the user My Account, “Security & privacy”, “Additional security verification”, “Create and manage app passwords”. In older versions of Office 365 the App Password option was in the title banner of the page, in larger font next to “Security Info”. It is now found by clicking on the “+ Add Method Button”, when available.
Links for O365 Modern Authentication articles by Microsoft:
Microsoft Modern Authentication: https://docs.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/set-up-multi-factor-authentication?view=o365-worldwide#enable-modern-authentication-for-your-organization
Exchange MA (includes how to connect with powershell): https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/enable-or-disable-modern-authentication-in-exchange-online
Alternate fix for missing o365 app password
Thanks to Jim Hill for sending these alternate fix steps which worked for him. You can see his original message in the comments. Cheers!
I figured out a solution! I am not sure if these are the exact steps I did. But the root cause was previously having a conditional access policy previously applied to that user.
-Make sure the CA policy for MFA is not enabled. Mine was the Legacy rule, “Baseline policy: Require MFA for admins (Preview)”
-Disable the MFA for that user in the Office 365 Admin.
https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx?BrandContextID=O365
-Create a new CA policy in Azure AD. Have it grant access and require MFA, and only apply just to that user.
-Go back to the Office 365 MFA admin and enable then disable the MFA requirement for that user a few times. I did it four times. Leave with it disabled.
-Return to Azure and remove that user from the CA policy requiring MFA. Leave it enabled but just not applied to any users.
-Return to Office 365 admin and enable MFA for that user.
-Initiate a screen sharing session with that user. Have them log into their MFA set up screen.
https://aka.ms/MFASetup They will then see and be able to create a new app password.This took me a month to figure out, and my exact steps may not have been exactly as I said above. Hopefully the whole community can figure out the best way.
Where can I manage Office 365 app passwords for multi factor?
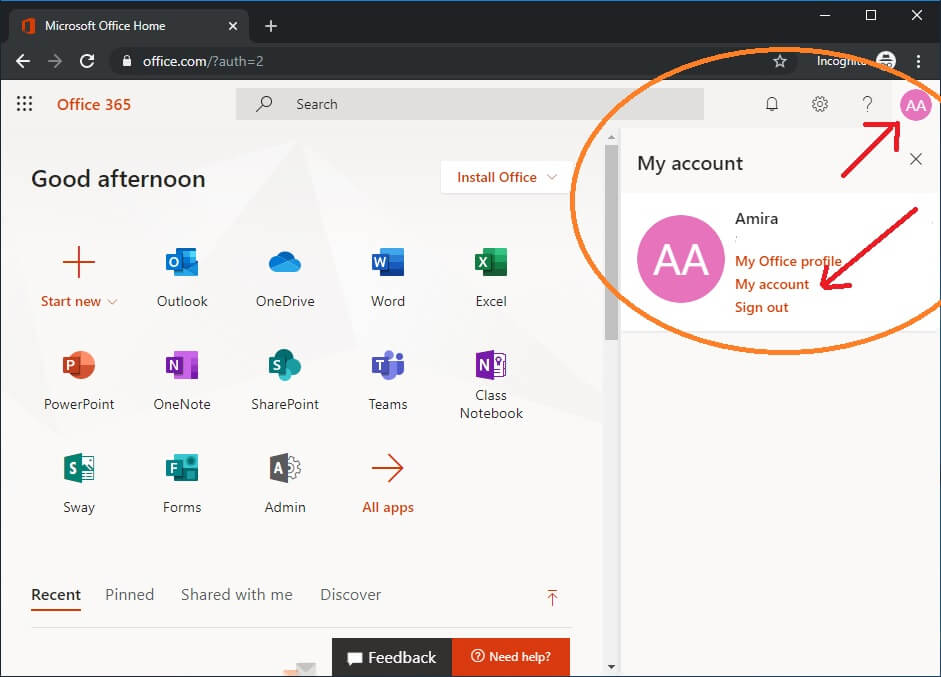
Log on to office.com with the user account that needs an app password
Click on your account icon at the top right corner (normally shows your initials)
Now click My Account
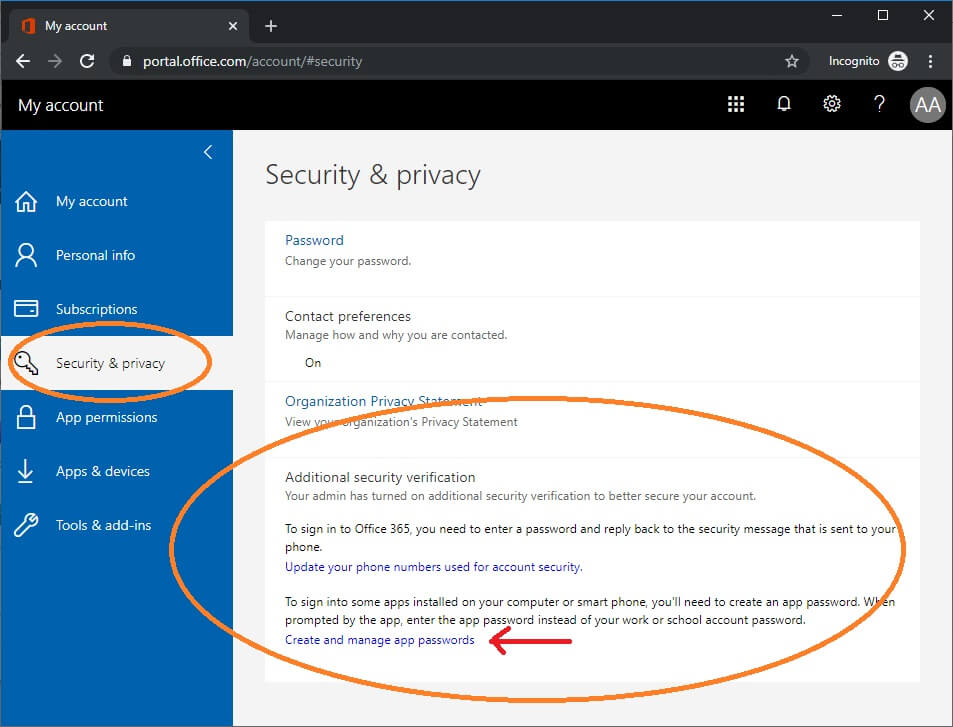
Click Security and Privacy
Expand Additional Security Verification
Click Create and manage app passwords
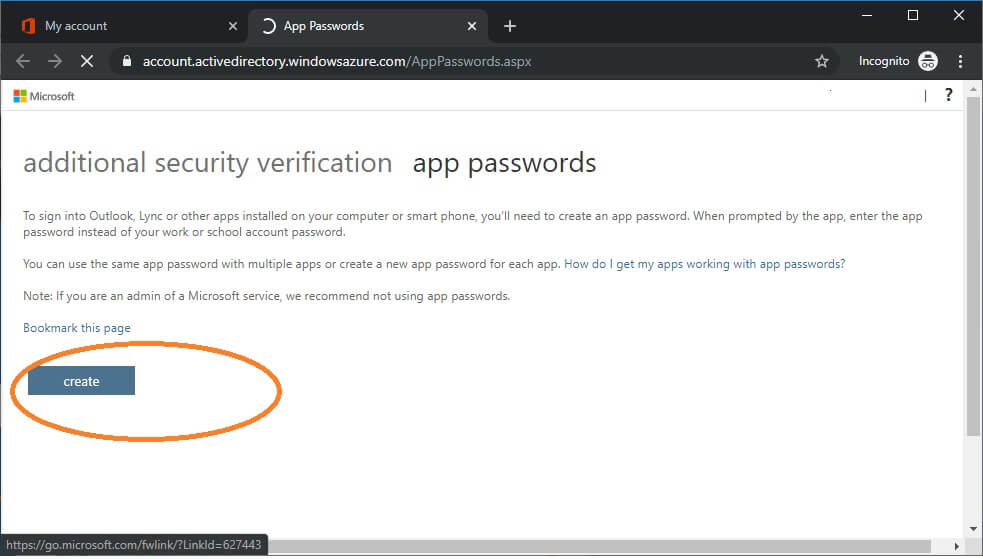
From here, you can create your app password.
This is what it is supposed to look like.


April 29, 2020 @ 7:52 am
That method did not work for me. And for many others I am afraid from what I read on the various forums.
I figured out a solution! I am not sure if these are the exact steps I did. But the root cause was previously having a conditional access policy previously applied to that user.
-Make sure the CA policy for MFA is not enabled. Mine was the Legacy rule, “Baseline policy: Require MFA for admins (Preview)”
-Disable the MFA for that user in the Office 365 Admin.
https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx?BrandContextID=O365
-Create a new CA policy in Azure AD. Have it grant access and require MFA, and only apply just to that user.
-Go back to the Office 365 MFA admin and enable then disable the MFA requirement for that user a few times. I did it four times. Leave with it disabled.
-Return to Azure and remove that user from the CA policy requiring MFA. Leave it enabled but just not applied to any users.
-Return to Office 365 admin and enable MFA for that user.
-Initiate a screen sharing session with that user. Have them log into their MFA set up screen.
https://aka.ms/MFASetup They will then see and be able to create a new app password.
This took me a month to figure out, and my exact steps may not have been exactly as I said above. Hopefully the whole community can figure out the best way.
April 29, 2020 @ 8:07 am
Thanks Jim! I moved your steps into the article body so that others will see it. Cheers!
July 30, 2020 @ 9:09 pm
I did finally find a way to fix this, once and for all, and not because of any help from Microsoft. They tried with no success. It is actually too simple, I could not believe it when I figured it out.
You just have to visit Office Admin, then Active Users. Don’t select a user. On the top select Multi-factor authentication. A new web page tab will open displaying the MFA status per user. For the user which cannot create app passwords you will see Enabled as the status. You must click that user and then select Enforce. The MFA was enabled but not enforced.
It is quite crazy, and drove me nuts for weeks. It works. I have MFA enabled through various CA policies and the Azure sign in policy (risky sign-ins require MFA).
January 26, 2021 @ 4:37 am
This worked for me, i did the steps above going into azure and disable the recommanded security feature that microsoft suggets.
in office 365 portal i could see that the task to enable mfa was unchecked. So i did what Jim said just go to mfa settings, enforce. and voila the option to add a app password appeard in de users profiel (the new my sign-ins)
Before this the user could only add a phone number or e-mail. Thank you so much
September 7, 2021 @ 9:08 pm
You’re a legend. I can go bandage my bleeding head, I’ve been banging on this wall for about 2 hours now. Thankyou thankyou thankyou!
January 19, 2022 @ 11:31 pm
Jim, you’re a ripper! thankyou for posting and contributing, your suggestion worked a charm,
July 10, 2022 @ 9:33 pm
Thank you sir, this was what fixed it for me.
July 31, 2022 @ 2:14 am
Legend! After months fighting with this, ensuring everything in Azure AD was set up correctly, this finally worked!
It’s bizarre that we need to force multi-factor authentication, which for all intents in purposes forces the user to use multi-factor otherwise, just to enable app passwords.
It’s finally working. For what it’s worth, I’m licensed as Microsoft 365 Business Basic for those who use O365 in a non-enterprise-y environment (refugee from the ol’ free GSuite days).
August 17, 2020 @ 12:21 pm
Despite all the above steps and comments, I still had trouble getting to the App password settings to create passwords. I found it in the past for a few of my users, but always had a difficult time retracing my steps and trying to Google the steps. However, today after being annoyed of not being to find it quickly and through a few attempts, I noted the steps that lead me to that screen.
To find it,
1) Sign in to office.com as the affected user.
2a) On the upper right, click on their initials or profile picture.
2b) Click “View account”
3a) A new tab opens
3b) The left column will show “Settings & Privacy” (this is where one would think app passwords are located–it’s not there.)
3c) Further down, click on “Office apps”
4a) Notice now the left column changes to “Security & privacy”
4b) Click on “Security & privacty”
5a) Click on “Additional security verification”
5b) Click on “Create and manage app passwords”
6) A new tab opens (that elusive screen reappears)
August 17, 2020 @ 12:23 pm
Great steps, thank you!
September 18, 2020 @ 8:03 pm
Just went round and round with this with MS tech support…
You have to disable MFA for the user. You have to manage settings and clear old APP passwords and require user to provide contact methods again. Then re-enable mfa and once contact methods are complete, you then have an option to add an APP Password.
Apparently, MS has a problem with the legacy APP passwords and the new and improved app passwords.
Please get word out and maybe this will help someone else! Cheers
November 11, 2020 @ 6:21 pm
Unfortunately there now seems to be an additional blocker to this. When you go to the Security and Privacy page (https://portal.office.com/account/#security) it now shows
“To update your password, contact preference or to view your organization’s Privacy statement go to your new My Account portal”.
Link goes to https://myaccount.microsoft.com/?ref=OfficePortalSecurityPrivacy
Settings and Privacy in the new Portal has only Language & Region and Privacy. So now no idea where App Passwords would be even were they to work with the workarounds above.
November 11, 2020 @ 6:47 pm
Actually wait. This has moved.
1. Go to My_Signins https://mysignins.microsoft.com/security-info
2. Go to Security Info
3. Click Add Method
4. Select App password
Again to reiterate that (currently) this only appears for users added/enforced directly in the Multi-factor authentication page in admin center. App password does not appear for users added to MFA via conditional policy.
December 22, 2020 @ 1:08 pm
Thank goodness for Peter Parker’s response on 11/11/2020. Microsoft really needs to update this information! This drove me crazy for two weeks!
January 11, 2021 @ 12:39 pm
This method has CHANGED.
1. Sign in to office.com as the affected user.
2. On the upper right, click on their initials or profile picture.
3. Click “View account”. A new tab opens
4. The left column will show “Security Info”
5. Click on “Add Method”
6. From the drop-down select “App Password” then click ADD
7. Give the App Password a name, such as “HP Scanner” then click NEXT
8. Copy your password to a safe place, that’s it!
March 10, 2021 @ 1:22 pm
Jay Lewis, i still don’t see the option under add a method to add an app password.
any thoughts?
April 16, 2021 @ 1:25 am
This really helped! Thank you everyone!
May 26, 2021 @ 2:45 pm
Changing the user to enforced fixed it for me also.
September 11, 2021 @ 2:29 pm
Despite this being the best page on the Internet for finding the App Password option in Office 365 (or now the almost-un-Googleable Microsoft 365), the instructions are wrong. Something has changed again.
The method to add an App Password does not appear under the “Add Method” drop-down. It’s just gone.
It doesn’t matter if the user has MFA enforced or not. It doesn’t matter if you clear old app passwords or turn on or off Modern Authentication. It doesn’t matter if you create a CA policy.
The option is simply gone like my youth, which I mis-spent on tracking down stuff like this.
September 30, 2021 @ 3:15 pm
I had a different experience than Ackley so I just wanted to add the steps used.
This is still working even with conditional access policy applied to all accounts.
Log in as Global Admin and access the following link:
https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx?BrandContextID=O365
(Not shown through modern UI)
Enable MFA for the user in question
Refresh page
Enforce MFA for the user in question
(Instructions below from Jay Lewis)
1. Sign in to office.com as the affected user.
2. On the upper right, click on their initials or profile picture.
3. Click “View account”. A new tab opens
4. The left column will show “Security Info”
5. Click on “Add Method”
6. From the drop-down select “App Password” then click ADD
7. Give the App Password a name, such as “HP Scanner” then click NEXT
8. Copy your password to a safe place, that’s it!
November 29, 2021 @ 3:54 pm
Wanted to second this response as I also ran into this. Any users that may have MFA as just enabled need to be set to enforced. As the article explained if the enables MFA with out it being enabled and enforced on the admin page app password would not appear as an option. As soon as they are enforced the option would appear.
July 7, 2023 @ 1:26 pm
Did not work for me. Only three options are available : Authenticator App, Email and Office phone.
February 25, 2022 @ 8:09 am
O365 App Password are found here as of 2-25-2022:
https://account.activedirectory.windowsazure.com/AppPasswords.aspx
July 7, 2023 @ 1:24 pm
That link redirects right back to the users settings where the option to create an App Password is still missing 🙁
January 18, 2023 @ 10:29 am
Any update on this issue?
App registration option is missing in authentication methods for a certain user. I only have AUTH APP, secondary phone, and office phone.
I saw this particular option some days ago but somehow its missing. Admin has the option but user has not.
I think I tried all methods written here:-(